Microsoft has plugged a critical hole in all supported versions of Windows that allows attackers to hit high-value computers with self-replicating attacks that install malicious code with no user interaction required.
The vulnerability in the Remote Desktop Protocol is of particular concern to system administrators in government and corporate settings because they often use the feature to remotely trouble-shoot e-mail servers, point-of-sale terminals and other machines when they experience problems. RDP is also the default way to manage Windows machines that connect to Amazon's EC2 and other cloud services. That means potentially millions of endpoints are at risk of being hit by a powerful computer worm that spreads exponentially, similarly to the way exploits known as Nimda and Code Red did in 2001.
"This type of vulnerability is where no user intervention or user action is required and an attacker can just send some specially crafted packets or requests, and because of which he or she can take complete control of the target machine," Amol Sarwate, director of Qualys' vulnerability research lab, said in an interview. While RPD is not enabled by default, he said the number of machines that have it turned on is a "big concern" because it is so widely used in large organizations and business settings.
The bug affects Windows XP and all versions of Windows released since, including the developer preview of Windows 8. It was privately reported by Luigi Auriemma, an Italian security researcher who frequently focuses on vulnerabilities in industrial control systems and SCADA, or supervisory control and data acquisition, systems used to control dams, gasoline refineries, and power plants. Microsoft said there's no indication the vulnerability is being used in the public to attack Windows users at the moment, but the company predicts that could change.
"Due to the attractiveness of this vulnerability to attackers, we anticipate that an exploit for code execution will be developed in the next 30 days," Suha Can and Jonathan Ness, of Microsoft Security Response Center Engineering, wrote in an advisory published Tuesday.
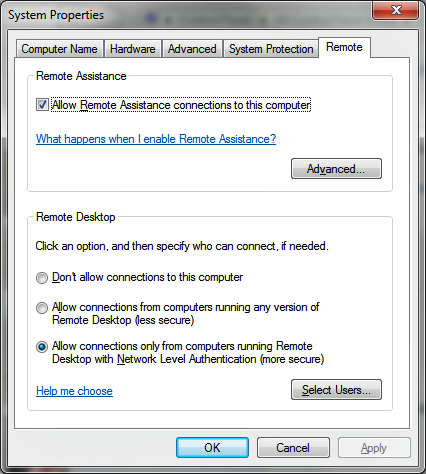
They urged users to "promptly apply" an accompanying security update. Those who can't update right away and are running Vista or a later version of Windows should enable Network Level Authentication, a feature that requires users logging in to RDP boxes to have security credentials before gaining access.
The RDP fix is one of six security patches Microsoft shipped as part of its most recent Patch Tuesday. In all, they fix at least seven vulnerabilities. Only the RDP bug is rated critical. Four bulletins were classified as important and one was rated as moderate.
Headline modified to add word "could."
Listing image by Photograph by Yun Huang Yong
reader comments
42