An estimated half million users of compromised computer systems risk losing their Internet connection next month unless a federal judge extends a court order authorizing a California not-for-profit to operate a network of surrogate domain-name-system servers.
Paul Vixie, founder of the Internet Systems Consortium, has been operating the servers since early November, when federal authorities obtained court permission for him to replace a fleet of rogue DNS resolvers used in a massive fraud scheme that directed millions of end users to websites they never intended to visit. Without the replacement servers, millions of people hit by the DNSChanger botnet would have experienced internet failures when the rogue systems were unplugged.
At a conference in San Francisco on Wednesday, Vixie said about 500,000 end users are still relying on the replacement servers to translate domain names into IP addresses. He made clear that if the court order expires on March 8 as it is now scheduled to do, his ISC non-profit, which maintains the open-source BIND DNS software package, will cease operating the replacement servers. And that will leave many of those still compromised in the dark.
"In the absence of that court order, it would be very difficult for someone like us to go in there and say, 'Yeah, we will speak BGP and pirate that address space and run these name servers,'" he told an audience attending the 24th General Meeting of the Messaging Anti-Abuse Working Group. "We will not do that. There are laws saying you should not but it's also just kind of a bad precedent."
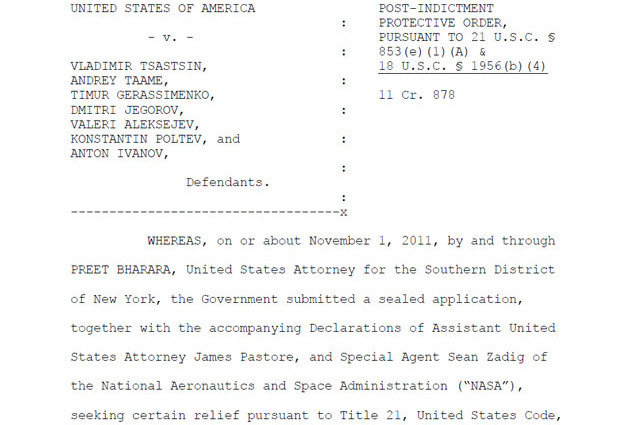
In a court document filed last week in US Court in the Southern District of New York, prosecutors asked that the order be extended by four months so authorities and network operators have additional time to notify customers who were infected by DNSChanger. The request comes after ISPs have told prosecutors that tens of thousands of their customers remain infected with DNSChanger, three months after the scam was exposed and seven of the principals behind it were indicted.
"Extending the operation of the Replacement DNS Servers will provide additional time for victims to remove the malware from their computers, thereby enabling them to reach websites without relying on the Replacement DNS Servers," the court motion states.
The predicament comes after federal prosecutors arrested six of the seven people alleged to be behind the DNSChanger scam. Using an Estonian business front dubbed Rove Digital, the team infected millions of windows PCs with a customized version of a highly virulent piece of malware known as Alureon, or alternatively as TDL or TDSS. The malware alters configuration settings in the operating system and unsecured wireless routers they connect to that cause people to use rogue DNS servers that were controlled by the perpetrators. As a result, those affected by the malware connected to Web servers they never intended to visit. The perpetrators earned millions of dollars in advertising revenue when the end users viewed ads on those sites, prosecutors said.
Under "Operation Ghost Click," authorities with the FBI and NASA's Office of Inspector General seized more than 100 US-based servers used to resolve popular domain names to incorrect IP addresses. To prevent millions of infected end users from losing the ability to access email and web pages, prosecutors arranged to have ISC simultaneously take over IP addresses and BGP, or border gateway protocol, addresses used by the rogue resolvers so the non-profit could set up replacement DNS servers.
Feds said at the height of the scam some 5 million machines were infected by the malware, although Vixie said that number may have been inflated because of the difficulty of mapping the number of IP addresses to PCs. He said he estimates 500,000 machines still rely on the replacement servers. Last week's court order put the figure at 430,000.
Vixie rejected audience proposals that, once the court order expires, ISC should redirect all people relying on the replacement servers to a "walled garden" page that informs them their systems are compromised. He also rejected a suggestion that the servers redirect users to such pages now, while the order is still in effect.
"That's not the business I'm in," he explained at the conference, which was attended by more than 400 representatives of ISPs, legitimate senders of bulk email, and vendors of software and hardware. "That's not the business the FBI is in, and I don't think that's what the judge thought he was authorizing. So at the moment, that looks to be completely off the table."
MAAWG Chairman Michael O'Reirdan told the audience member that ISPs are working hard to alert customers who remain infected so they can clean up their machines.
"If putting people in walled gardens doesn't work, we're going to do something else," he said. "If the most effective thing to do is send them individual carrier pidgins, maybe that's what we'll have to do in the future."
Listing image by Photograph by kenjonbro
reader comments
71